TPRM compliance
Compliance expectations have changed. Regulators, boards, and customers no longer settle for a once-a-year audit or a static vendor questionnaire – they expect proof of compliance that’s always accurate, always current.
The problem? Traditional audits and point-in-time reviews are slow, manual, and outdated the moment they’re complete. That means gaps, delays in procurement, and endless hours chasing vendors for paperwork.
What’s needed is a shift in how compliance is managed. Third-party risk programs must evolve from static, reactive checklists to dynamic, continuous monitoring that delivers real-time visibility into vendor posture. Only then can security and compliance teams keep pace with modern business expectations while reducing both risk and workload.
What is TPRM compliance?
Third-party risk management (TPRM) compliance is the process of verifying that your vendors and partners meet security, privacy, and regulatory obligations. It ensures that the organizations you rely on handle sensitive data responsibly, adhere to industry standards, and reduce risk across your supply chain.
In practice, third-party compliance management involves collecting vendor evidence, mapping it to frameworks like SOC 2, ISO 27001, NIST CSF, HIPAA, and GDPR, and maintaining an audit-ready trail. Historically, this was handled through static questionnaires and annual audits, but these point-in-time approaches can’t keep up with today’s pace of change.
That’s why many teams are moving toward a modern AI compliance solution for third-party vendor management—one that continuously gathers information, monitors for changes, and provides real-time visibility into vendor compliance posture. With this shift, TPRM compliance becomes less about checking boxes and more about sustaining trust, resilience, and operational efficiency.

Why faster, automated assessments matter
Organizations face mounting pressure to vet hundreds or thousands of vendors. Manual assessments can’t keep up.
Weeks of delay
Traditional third-party vendor risk assessments take 3–12 weeks, slowing projects and exposing your environment.
Manual chasing
Security teams spend time emailing vendors, tracking spreadsheets, and reconciling SIG assessments or vendor security assessment questionnaires.
Fragmented data
Evidence lives across inboxes, portals, and files, with no single view for stakeholders.
Limited coverage
Many programs rely on surface-level scans or self-attested data, missing critical risks.
Audit pressure
Without a repeatable process or evidence trail, proving due diligence to auditors or boards is hard.
Slow response to emerging risks
Even after completing an assessment, following up on recommendations or newly discovered issues (like a breach advisory) is time-consuming and inconsistent.
Types of compliance risks
When it comes to third-party risk management, “compliance” isn’t one-size-fits-all. Vendors can introduce different kinds of risks depending on the data they handle, the industries they serve, and the regulations that apply. The main categories include:
Regulatory risk
Vendors must comply with laws and mandates such as GDPR, HIPAA, or CCPA. A missed requirement can put your organization at risk of legal penalties and reputational damage.


Framework risk
Standards like SOC 2, ISO 27001, and NIST CSF provide structured ways to prove security and compliance. If a vendor can’t maintain these certifications—or if evidence goes out of date—you’re left without assurance that the relevant controls are not in place..
Operational and contractual risk
Even if a vendor is technically compliant, lapses in how they manage data, staff, sub-service providers or where they do business and store data can create hidden exposure. These gaps often emerge in contracts, SLAs, or internal policy misalignments.

Understanding these categories helps organizations prioritize monitoring and tailor oversight based on the type of compliance risk most relevant to each vendor.
Business outcomes of automated compliance
The shift from manual, point-in-time audits to continuous, automated TPRM compliance delivers impact well beyond the security team. Organizations see:
Faster vendor onboarding
Procurement moves quickly when compliance status is always current and audit-ready.
Reduced audit costs and surprises
Continuous validation means fewer findings and less fire-drill prep.
Improved trust with stakeholders
Boards, regulators, and customers gain confidence in proactive oversight.
Greater operational resilience
Compliance gaps are spotted and fixed before they become incidents.
More time for strategic risk management
Automation frees teams from chasing paperwork, allowing them to focus on higher-value initiatives.
These outcomes demonstrate that TPRM compliance is no longer just a check-the-box exercise—it’s a driver of efficiency, trust, and resilience across the business.
Best practices for TPRM compliance
Modern TPRM compliance programs succeed when they balance automation with clear processes. A few proven practices include:
Standardize evidence collection
Replace scattered emails and spreadsheets with centralized intake of vendor documents and attestations
Map once, reuse everywhere
Align vendor controls to multiple frameworks simultaneously so evidence can serve SOC 2, ISO, HIPAA, and GDPR requirements without duplication
Track meaningful metrics
Focus on KPIs like average time to verify vendor compliance, percentage of vendors with current evidence, and the number of critical control gaps identified and closed
Avoid common pitfalls
Be mindful of alert fatigue, fragmented toolsets, and inconsistent documentation. These issues make it harder to prove oversight.
Integrate into workflows
Feed compliance updates into tools your teams already use—like ServiceNow, Jira, or Slack—so monitoring and remediation become part of everyday operations
By following these practices, organizations can build a compliance program that’s both efficient and defensible.
How VISO TRUST transforms vendor management compliance
Combine continuous evidence collection, AI-powered analysis, and framework mapping to give an always-current, audit-ready view of vendor risk.
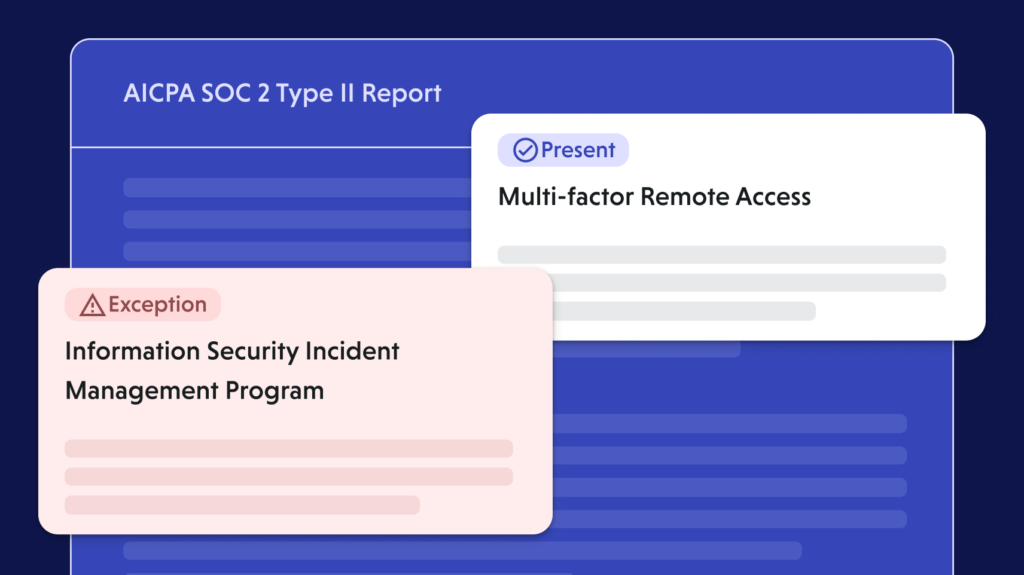
Continuously collect vendor evidence
Automate the intake of documents like SOC 2, ISO 27001, HIPAA, and GDPR certifications—no more chasing vendors.
Validate controls with automated assessments
Use AI-driven risk assessment tools to check evidence against security and compliance requirements in minutes.
Map once, report everywhere
Align vendor controls to 30+ frameworks with dynamic mapping that produces exportable, audit-ready reports.
Spot issues before they become findings
AI compliance monitoring surfaces risks proactively so you can remediate early and avoid audit surprises.
Stay audit-ready at all times
Provide leadership, boards, and regulators with instant, verifiable reports that prove compliance without extra effort.
Integration-ready
Streamline and automate complex workflows and decision-making across your entire enterprise stack – seamlessly integrating with tools like Jira, Coupa, ServiceNow, Archer, Slack, Okta, and thousands more.

Benefits of automated TPRM compliance with VISO TRUST
Audit-ready in minutes, not months
Deliver exportable, regulator-ready reports instantly instead of waiting weeks for manual reviews.
Clarity across every framework
Always know which vendors align to which standards—SOC 2, ISO 27001, HIPAA, GDPR, and more.
Less chasing, more oversight
Eliminate endless spreadsheets and manual follow-ups with automated evidence collection.
Prove compliance at every level
Show regulators, boards, and customers a continuous record of third-party oversight.
Defensible records you can trust
Maintain a living, audit-ready history of vendor controls, alerts, and remediation actions.
