Third-party cybersecurity metrics for the board
Boards and executives are under growing pressure to oversee third-party and supply chain risk, but the data they receive often falls short. Traditional vendor risk assessment reports are built from static spreadsheets and scattered tools, leaving leaders with outdated snapshots instead of real visibility. Requests for updates turn into last-minute scrambles, and technical details rarely translate into clear, actionable insights.
That gap is where cybersecurity metrics for the board come in. By turning third-party assessments, incidents, and program data into consistent, evidence-backed reporting, organizations can give leadership the oversight regulators expect and the clarity decision-makers need. Done right, board-level reporting transforms third-party risk from a compliance burden into a strategic advantage.
What is executive and board reporting in TPRM?
Executive and board reporting in third-party risk management (TPRM) is the process of turning raw risk data into clear, actionable insights. Rather than handing over questionnaires or spreadsheets, risk teams produce polished cybersecurity risk management reports that highlight:
- Current vendor posture
- Program-wide risk levels
- Trends in compliance or supply chain resilience
- Summaries of any cybersecurity incident reports or findings
Done right, these reports help leadership understand the big picture—vendor risk across the ecosystem, software supply chain security reports, and even enterprise-wide metrics. This shifts reporting from a “check-the-box” task to a vital input for enterprise risk management reports and strategic oversight.
Why software supply chain security reporting is painful without automation
Weeks of delay
Risk teams spend hours stitching together vendor risk assessment reports and dashboards. The result is heavy lift for data that’s already going stale.
Manual chasing
By the time leadership sees a cybersecurity board report, incidents may have already passed or compliance gaps may have widened—making oversight reactive instead of proactive.
Fragmented data
Key metrics live across assessment tools, monitoring feeds, and ticketing systems. Without a unified view, it’s nearly impossible to generate a reliable software supply chain security report.
Limited coverage
Boards and regulators now expect continuous, evidence-backed proof of oversight across all third-party service providers—not just an annual slide deck.
Audit pressure
Raw data and technical jargon don’t translate directly into cybersecurity metrics for the board. Without context, executives struggle to make informed decisions.
Types of risk boards need to see
When reporting third-party risk to executives and boards, it helps to break the concept into clear, tangible categories. Risk isn’t abstract—it shows up in specific ways that can (and should) be measured.
Cyber risk
This is often the most visible concern. It includes breaches, vulnerabilities, exposed credentials, and poor security practices by vendors. A strong cyber security risk assessment report should highlight these issues with context: what happened, which vendor is impacted, and how it affects your business. These insights form the backbone of credible cybersecurity board reporting.


Compliance risk
Vendors are expected to maintain attestations like SOC 2, ISO 27001, HIPAA, and GDPR. If certifications expire or evidence is incomplete, your organization inherits that gap. Board-level reporting should surface these compliance shortfalls clearly—turning technical findings into actionable cybersecurity metrics for the board.
Operational and supply chain risk
Even a compliant vendor can cause disruption if it suffers an outage, ownership change, or supply chain dependency issue. Boards increasingly expect software supply chain security reports and supplier risk reports that capture these vulnerabilities alongside cyber and compliance data.
Together, these categories give leadership a complete view of third-party exposure. When framed through a polished vendor risk assessment report or enterprise risk management report, they show not just what risks exist, but how those risks affect resilience, continuity, and trust across the business.

Breaking risk into these categories helps organizations move beyond static questionnaires toward a living, dynamic view of vendor posture. With AI-powered assessments, these risks aren’t just identified—they’re continuously monitored, contextualized, and prioritized so teams can act before small issues become major problems.
Business outcomes of executive & board reporting
The impact of clear, board-ready reporting extends far beyond saving time on slides and spreadsheets. Organizations that elevate third-party risk reporting achieve:
Better decision-making
with timely cybersecurity risk assessment reports that translate technical findings into business context.
Faster incident response
through on-demand cybersecurity incident reports that give executives clarity when it matters most.
Stronger oversight
of third-party service providers, backed by defensible, evidence-based metrics.
Greater trust and transparency
with boards, regulators, and customers through consistent, polished reporting.
Improved efficiency
as security teams spend less time compiling data and more time managing risk.
These outcomes shift executive and board reporting from a reactive compliance burden to a strategic driver of resilience, alignment, and business confidence.
Best practices for executive & board reporting in TPRM
Turning third-party risk data into board-ready insights requires more than good intentions—it takes process, consistency, and the right approach. Whether you’re building reporting from scratch or maturing an existing program, these best practices help ensure executives get the clarity they need.
Standardize your reporting framework
Define a consistent set of cybersecurity metrics for the board—covering vendor risk assessments, incidents, and program-wide trends. Consistency builds trust and makes it easier to compare results over time.
Translate technical details into business language
Executives don’t need raw logs or jargon. Convert findings into narratives and visuals that explain impact on the business, using cybersecurity risk assessment report templates or dashboards tailored for leadership.
Automate wherever possible
Manual prep leads to errors and delays. Use tools that can generate vendor risk assessment reports and cybersecurity incident reports directly from program data, reducing the risk of outdated or incomplete insights.
Include incidents and response
Don’t just report on static posture. Incorporate cybersecurity incident reporting best practices—what happened, the response, and current status—so leadership sees oversight in action.
Align reporting cadence with business needs
Move beyond annual updates. Deliver quarterly cybersecurity board reports, monthly roll-ups, or on-demand incident response report examples so executives always have current visibility.
By following these practices, organizations can replace reactive, last-minute updates with reliable, proactive cybersecurity executive board reporting that strengthens oversight and builds confidence across the business.
When applied thoughtfully, AI-powered assessments shift vendor risk management from a reactive compliance exercise into a continuous, scalable driver of resilience.
How VISO TRUST delivers board-ready vendor risk assessment reports
VISO TRUST transforms raw assessments and monitoring signals into polished, defensible reporting that boards and executives can act on. With automation at the core, teams get instant clarity instead of manual prep:
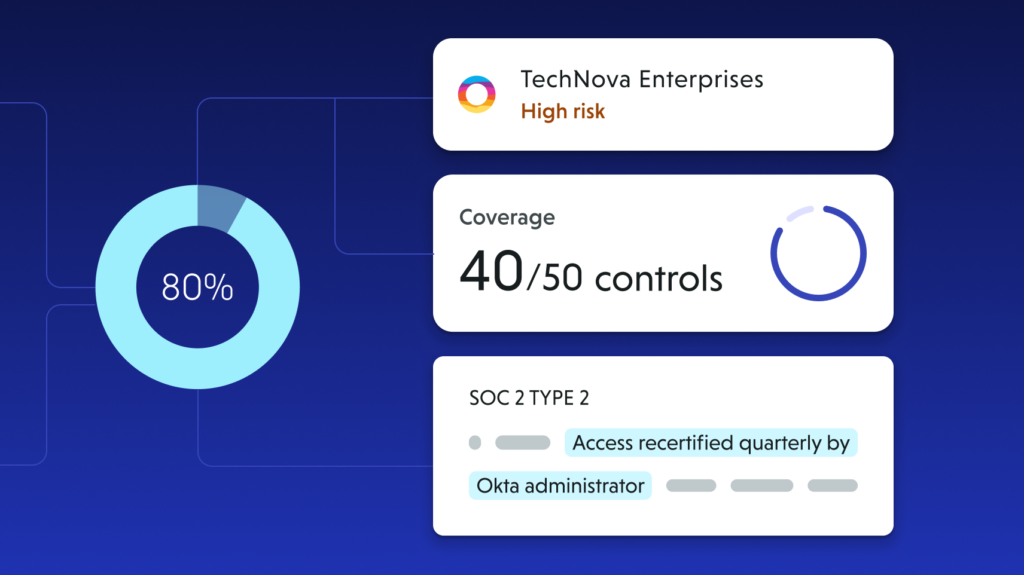
AI-generated smart summaries
Pulls context from assessments, artifacts, and controls to create stakeholder-ready reports instantly.
Customizable, exportable reports
Customize language, branding, and layout before sharing with leadership or auditors.
On-demand incident reporting
When vendor monitoring flags a breach, create an executive-level cybersecurity incident report instantly—summarizing the issue, impact, and next steps.
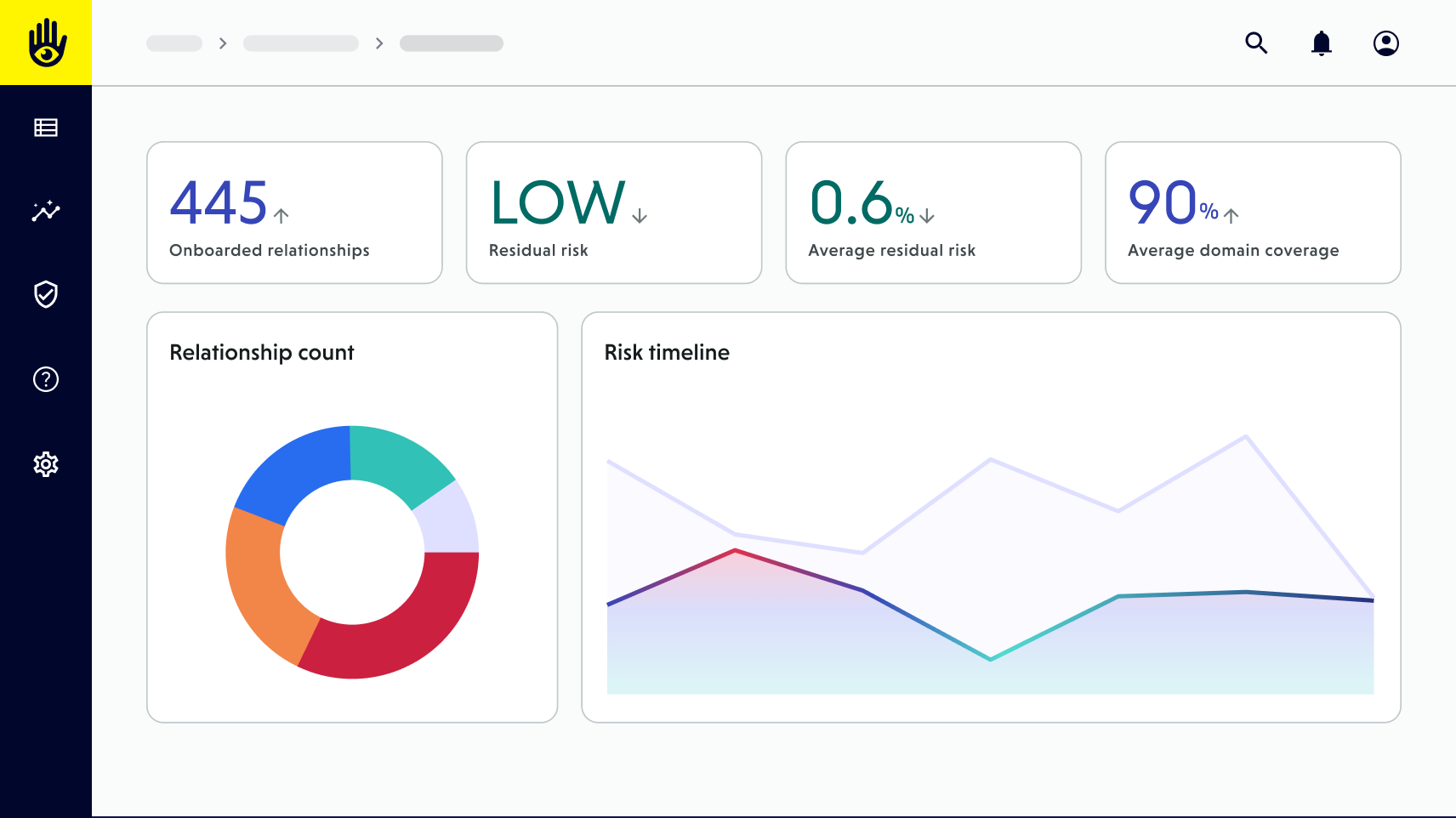
Program-wide risk insights
Use Risk Insights to filter by risk level, vendor type, or business unit and produce annual cybersecurity reports or quarterly board updates.
Unified oversight of third parties
Consolidate security posture, compliance evidence, and monitoring alerts across your vendor ecosystem in one dashboard, providing continuous visibility to leadership.
Integration-ready
Streamline and automate complex workflows and decision-making across your entire enterprise stack – seamlessly integrating with tools like Jira, Coupa, ServiceNow, Archer, Slack, Okta, and thousands more.

Benefits of executive & board reporting with VISO TRUST
Board-ready in minutes
Produce polished cyber security risk assessment reports instantly, not weeks later.
Audit-ready at any time
Every alert, artifact, and decision is traceable in the exported report, ensuring compliance with regulators and auditors.
Clear communication for leadership
Translate technical details into concise narratives and visuals that boards can act on.
Scalable visibility across the program
Roll up thousands of assessments into a single, credible view with filters by risk level, vendor type, or business unit.
