PCI risk assessments
Simplify PCI DSS v4.0 vendor assessments with automated evidence intake and continuous monitoring.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a global standard from the PCI Security Standards Council (PCI SSC). It applies to entities that store, process, or transmit payment account data — and to third-party service providers (TPSPs) that can affect the cardholder-data environment (CDE).
Validation is performed via SAQ (self-assessment) or by a QSA resulting in a ROC and AOC.
Common control areas
Network security and segmentation, secure configurations, protection of stored data, strong cryptography in transit, anti-malware and patching, access control and authentication, logging and monitoring, vulnerability management and penetration testing, incident response, and governance.
Typical artifacts
AOC/ROC or applicable SAQ, network/data-flow diagrams, segmentation evidence, ASV scan reports, penetration-test reports, vulnerability findings and remediation, key-management procedures, logging/monitoring summaries, incident response plans, and TPSP responsibility matrices.
PCI DSS requirements for third-party risk
12.8.1
Maintain an accurate
TPSP inventory List service providers and the services they deliver.
12.8.2/12.9
Use written agreements with responsibility acknowledgements
Contracts must state the provider’s responsibility for cardholder data they handle or can impact.
12.8.3
Perform formal due diligence before engagement
Assess scope and controls prior to onboarding.
12.8.4
Monitor compliance at least annually
Track current AOC/ROC or applicable SAQ.
12.8.5
Document shared responsibilities
Maintain who manages which PCI DSS requirements (e.g., RACI/responsibility matrix).
In practice
Define TPSP scope clearly
Establish clear boundaries for what third-party services are in scope for PCI DSS requirements.
Verify assessments cover your services
Ensure that vendor assessments actually cover the specific services you consume.
Enforce contract obligations
Include incident notification, right to assess, reporting cadence, and subprocessor disclosure in agreements.
Monitor expirations and changes
Track certificate expirations, scope changes, and material updates to vendor environments.
Coordinate incident response
Establish clear procedures for incident notification and coordinated response with vendors.
Keep audit-ready records
Maintain comprehensive documentation that’s always ready for internal or external audits.
Challenges in manual PCI DSS assessments
Evidence scattered across emails and spreadsheets
Manual tracking makes it difficult to maintain a comprehensive view of vendor compliance documentation and status.
SAQ selection and TPSP scope confusion
Determining the right self-assessment questionnaire and understanding vendor scope can be complex and error-prone.
Slow follow-ups and unclear ownership
Without automated workflows, tracking responsibilities and following up on missing evidence creates delays.
Inconsistent reviewer scoring
Different reviewers may assess the same evidence differently, leading to inconsistent risk evaluations.
Limited visibility into subcontractors or sub-providers
Understanding the full chain of payment processing and data handling across sub-providers is challenging.
Assurance that goes stale between annual validations
Point-in-time assessments don’t capture changes, incidents, or expired certifications between review cycles.
How VISO TRUST streamlines PCI vendor validation
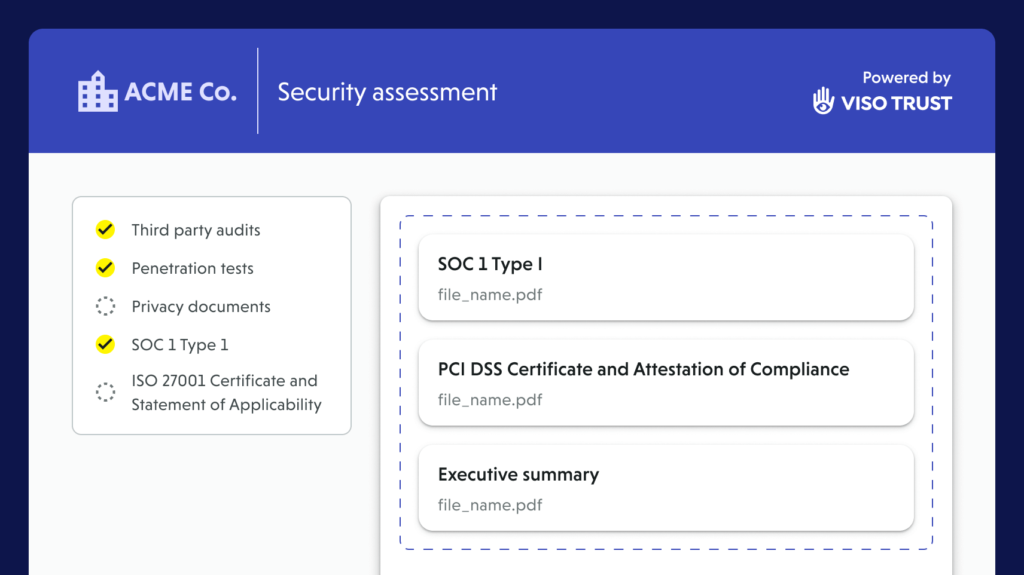
Automated artifact collection
Request exactly what’s needed for PCI DSS v4.0 – AOC/ROC, data-flow and network diagrams, segmentation evidence, ASV and pen-test reports, vulnerability findings and fixes, key-management docs, logging/monitoring summaries, incident procedures, and TPSP responsibility matrices. Portfolio-wide campaigns handle outreach and expirations automatically.
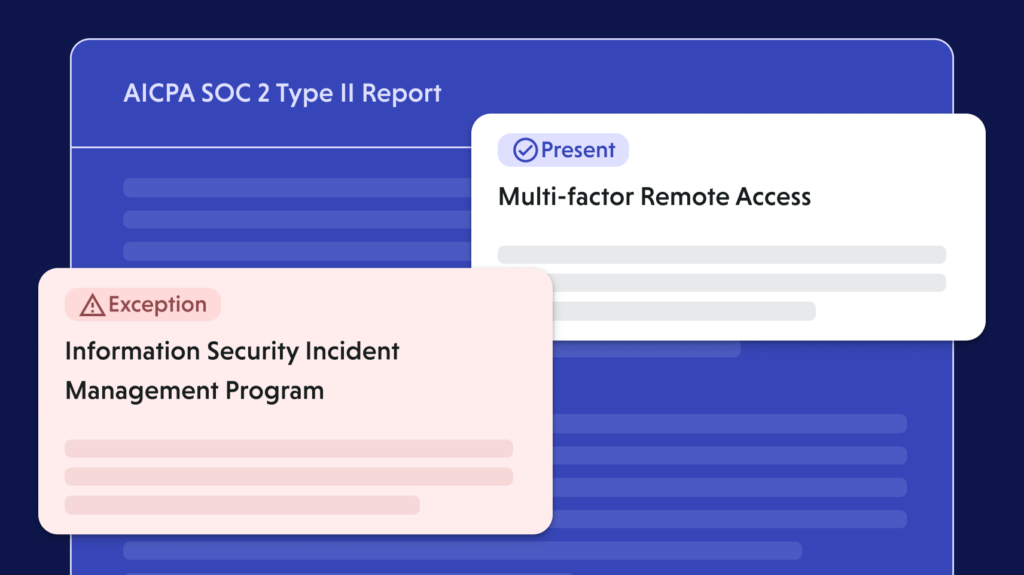
Evidence validation
Artifacts are parsed and linked to the 12 PCI DSS requirements. Signals are scored with rationale, gaps, and remediation guidance, powering consistent PCI compliance reporting.

Targeted risk analyses (v4.0)
Where v4.0 allows flexibility (e.g., customized approaches/frequencies), run defensible analyses that justify cadence and controls – keeping your PCI DSS risk assessment auditable.
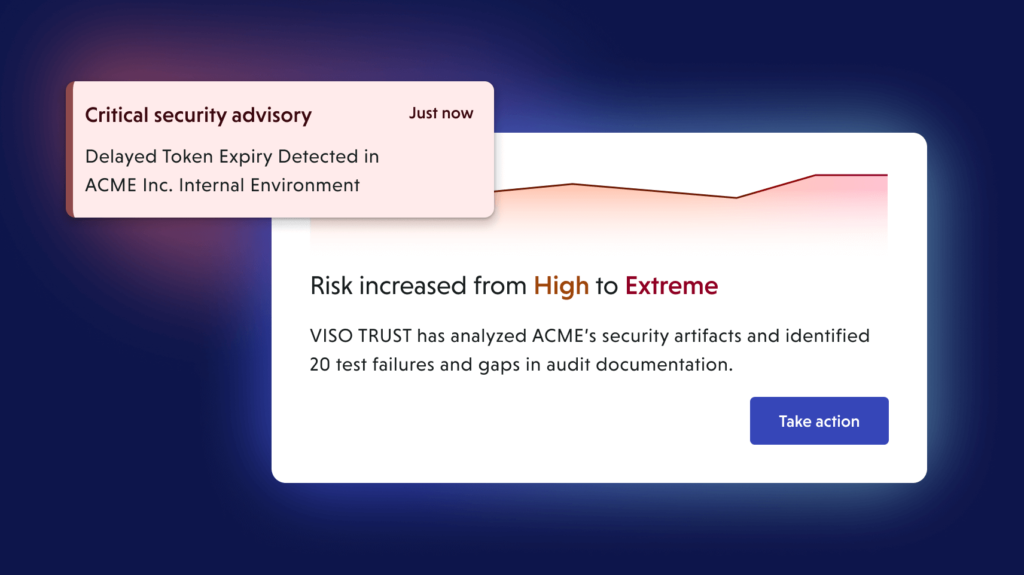
Continuous assurance
Track expirations (AOC, ASV), material changes, incidents, and sub-provider updates. Trigger re-checks automatically instead of waiting for annual cycles.
Frequently asked questions
Stop chasing evidence. Start proving PCI DSS compliance.
Talk to us about automating your vendor risk assessments.